In a Firewall device, there could be numerous rules/access-list defined to secure the network from external attacks. Out of the rules/access-list configured, there could be certain rules which would be most used and certain which are least used or never used. Firewall Analyzer captures the most used rules in the Top Used Rules as they would be available in the logs generated by Firewall. But, to get the Unused Rules, one needs to configure the Firewall Analyzer to fetch the complete rules from the device. Once, Firewall Analyzer fetches the complete rules configured in the Firewall, it can provide the Unused Rules view.
To view Unused Firewall Rules, configure the Firewall Analyzer by following the steps given below:
- In the Firewall Analyzer web client, select the Settings tab.
- In Settings screen, select the Firewall > Firewall Server > Device Rule link. Device Rule Info page appears.
Device Rule Info
Sophos XG Firewall provides unprecedented visibility into your network, users, and applications directly from the all-new control center. You also get rich on-box reporting and the option to add Sophos iView for centralized reporting across multiple firewalls. Click here to view list of all features supported by Sophos XG Firewall. 查看 Elastic Stack(Elasticsearch、Kibana、Beats 和 Logstash)就地部署、Elastic Cloud 和 Elastic Cloud Enterprise 的订阅级别、定价和分级功能。. Sophos XG Firewall: How to configure SSL VPN remote access KB-000035542 01 21, 2021 97 people found this article helpful. Overview This article describes the steps to configure SSL VPN remote access. The following sections are covered: Configuring Sophos Firewall. Defining SSL VPN group and users. Netflow Netflow allows you to add, update, or delete Netflow servers. The device offers Netflow, a network protocol, to monitor network bandwidth usage and traffic flow. Netflow records of source, destination and volume of traffic are exported to the Netflow server. Sophos XG Firewall 4 Synchronized Security Security Heartbeat™ - Your firewall and your endpoints are finally talking Sophos XG Firewall is the only network security solution that is able to fully identify the user and source of an infection on your network and automatically limit access to other network resources in response.
Device Rule
After entering and saving the Device Info values through the Firewall Analyzer GUI, the device, with details to fetch rules, is listed in the Device Details table. The details of the columns of the Device Details table are:
| Device Rule | Description |
|---|---|
| Status | The status of fetching device rules/access control of the Firewall device |
| Devices Name | The names of the devices for which the rules will be fetched |
| Virtual FWs | For multi (vdom/context) Firewalls, this will display the number of vdoms/contexts associated to this specific device rule. Clicking on the count will show the details of the vdoms/contexts individually. Refer the screen shot below. |
| Security Audit | The configuration changes of the Firewall devices are reported. The report is available on clicking the link and the link text shows the time the configuration change report was generated. You can instantly fetch the current configuration change report by clicking the icon. |
| Config Changes | The configuration changes of the Firewall devices are reported. The report is available on clicking the link and the link text shows the time the configuration change report was generated. You can instantly fetch the current configuration change report by clicking the icon. |
| Last Update On | The time when the rules of the device were updated last. |
| On Demand |
|
| Status | Enable, disable notification |
| Edit | An icon to edit the details of the rules fetching info of the device. Click icon to edit the device info. |
Virtual Firewalls
- When you click the Virtual FWs number displayed in the Device Details list you will see the details of the virtual domains in a pop-up window which will provide you with all the options.
Add Device Info
- Click the Add button to add the device information to fetch the rules and configurations using CLI, API or File. The Add Device Credentials screen opens up.
- Select the Firewall device in the Select Device drop down list.
- In the Fetch Through drop down list, there will be two options to fetch rules and configurations
Select the option as per your requirement.
- If you want to use a credential profile, choose from the listed profile. You can add a new profile using the green + button.
- In the Credentials field, enter either Primary or Primary and Additional credentials using Primary and Additional radio buttons.

Manageengine Netflow Analyzer
The Credentials tab
You can configure the individual device credentials to fetch the rules and configuration from the device or you can create a common profile of device credential which can be used for a group of devices to fetch rules.
| Note: | Fetching the rules directly from the device is supported for the following devices only:
For the rest of the devices, please use the Fetch Rules/Config > From File option. |
Fetch Through > CLI
Primary - deal with parameters that are necessary to establish communication with the device. Details such as Login Name, Password, Prompt, Enable UserName, Enable Password and Enable Prompt are classified as basic details.
Device Info | Description |
|---|---|
| Protocol | Select the protocol (SSH, Telnet, SSH TFTP, Tlenet TFTP) in the Protocol drop down list. |
| Firewall IP Address | Enter IP address of the firewal for credential configure. See Note below. |
Login Name | While establishing connection with a device, if the device asks for a Login Name, set a value for this parameter. This parameter is Optional. |
Password | To set the Password for accessing the device. |
Prompt | The prompt that appears after successful login. Ntfs for mac os 10. |
| Enable Command | The command to fetch the rule and configurations |
Enable UserName | When entering into privileged mode, some devices require UserName to be entered. Provide the username if prompted; otherwise leave this field empty. |
Enable Password | This is for entering into privileged mode to perform configuration operations like backup/upload. This parameter is mandatory. |
| Enable Prompt | This is the prompt that will appear after going into enable mode. |
| Note: | Both Primary and Additional credentials (Login Name and Password) of the Firewalls are encrypted and stored in the Firewall Analyzer. |
Additional - certain parameters usually take standard values. All such parameters have been classified under 'Secondary Info'. Port, login prompt, enable user prompt, password prompt, enable password prompt values are usually assigned with certain Standard Values by default. Such standard values have been filled for these parameters. Most of the devices would work well with these values and you need not edit these details unless you want to provide different set of details.
All the parameters are usually assigned with certain Standard Values by default. Such standard values have been filled for these parameters. Most of the devices would work well with these values and you need not edit these details unless you want to provide different set of details.
Device Info | Description |
|---|---|
| Port (Telnet/SSH) | Port number of Telnet/SSH - 23 (for Telnet) and 22 (for SSH) by default. |
Login Prompt | The text/symbol that appears on the console to get the typed login name is referred as login prompt. For example, Login: |
Password Prompt | The text displayed on the console when asking for password. For example, Password: |
Enable User Prompt | The text displayed on the console when asking for Enable UserName. For example, UserName: |
Enable Password Prompt | The text displayed on the console when asking for password. For example, Password: |
| Banner Prompt | The prompt that appears for the banner |
| Banner Input | The banner message |
- Click Validate button, to test the validity of the device info.
- Select the Schedule Rules/Config Fetching check box to fetch the rules/configurations periodically or once. Select the periodicity of rules fetching from the combo boxes given in: Every <1 to 31> day(s) @ <0 to 23> Hrs <0 to 50> Min. (For example: If you configure like Every 10 day(s) @ 2 Hrs 30 Min, the rules will be fetched from the device, every 10 days at 02:30 AM).
- Click Save button to apply the values.
| Note: | If the Firewall Analyzer is not receiving the logs directly from the Firewall device (i.e., the logs are received from a log forwarder tool), to fetch the rules from the Firewall device, configure the IP Address of the actual Firewall. Configure the IP Address, using Primary > IP Address field. |
| Note: | Generating Change Management Report is supported for the following devices:
|
| Note: | Getting Rules/ Configuration Information from the individual virtual firewalls (vdom/context)
|
Fetch rules for Check Point devices
- Click the Add button to add the device information to fetch the rules and configurations using CLI, API. The Add Device Credentials screen opens up.
- Select the Firewall device in the Select Device drop down list.
Check Point firewall version 80.10 or later with CEF log format cases, we have only option to get IP address value from syslog, in these cases using IP address we can't findout the gateway specific rules, so must provide Gateway Name value to get gateway specific rules. - In the Fetch Through drop down list, there will be two options to fetch rules and configurations
Select the option as CLI.
Fetch Through CLI
Device Info | Description |
|---|---|
| Select Device | Select the IP address or device name of the Check Point firewall device. |
| Fetch Through | Select CLI from the CLI, API, File drop down list. |
| Protocol | Select the SSH protocol (SSH, Telnet) in the Protocol drop down list. |
| Port | Select port 22 from the 22, 23 drop down list. |
Management Server Info | Description |
|---|---|
| Management Server IP | Enter IP address of the Check Point firewal Management Server. |
Login Username | While establishing connection with a device, if the device asks for a Login Username, enter the Username of the device. |
Login Password | Enter the Login Password for accessing the device. |
| Security Management Administrator Username | While establishing connection with a Management Server of the Check Point device, if the device asks for a Security Management Administrator Username, enter the login name of the device. |
| Security Management Administrator Password | Enter the Security Management Administrator Password. |
Prompt | The prompt that appears after successful login. |
| Timeout | The time allowed to login to the device successfully. |
Gateway Name | Enter the Gateway Name. |
Domain Name | Select the Domain Name check box. Enter the domain name. |
- Click Validate button, to test the validity of the device info.
- Select the Schedule Rules/Config Fetching check box to fetch the rules/configurations periodically or once. Select the periodicity of rules fetching from the combo boxes given in: Every <1 to 31> day(s) @ <0 to 23> Hrs <0 to 50> Min. (For example: If you configure like Every 10 day(s) @ 2 Hrs 30 Min, the rules will be fetched from the device, every 10 days at 02:30 AM).
- Click Save button to apply the values.
Fetch Through > File
- In the File selection, you will find the two options: Import Rule File and Import Configuration File.
- In the Import Rule File option, click the Browse button to locate the file which contains the rules details of the Firewall device.
- In the Import Configuration File option, click the Browse button to locate the file which contains the complete configuration details of the Firewall device.
- Click Import button to import the rule/configuration file. Click Cancel to cancel the rules/configuration details file importing operation.
Only for Check Point Firewall
- In the case of Check Point firewalls, there will be multiple configuration files. In that case, if you are using 'From File' mode, it should be provided in the Zip file format.
- The configuration files are:
- objects.C
- objects.C_41
- objects_5_0.C
- rules.C
- rulebases.fws
- rulebases_5_0.fws
- The files are stored in the directory conf or database.
| Note: | Rule File
Configuration File
|
| Note: | Getting Rules/ Configuration Information from the individual virtual Firewalls (virtual domain) If you want to fetch the rules/configurations from the individual virtual Firewalls (virtual domain) separately, select the option 'Display Virtual Domains in the below resources list.' in Associate Profiles to Devices page. It lists both the virtual Firewalls (virtual domain) and the physical devices in the Select Device drop down list. |
| Note: | Trouble Shooting: If the following message appears in the Compliance Reports field, enable Nipper. 'Unable to generate compliance report. Reason: failed to locate nipper. Click here to enable it' |
Fetch Through > API
- In the API selection, enter the Device Info.
Primary - deal with parameters that are necessary to establish communication with the device. Details such as Login Name, Password, Prompt, Enable UserName, Enable Password and Enable Prompt are classified as basic details.
Primary Info
Device Info | Description |
|---|---|
Web Server URL | URL of the API management server of the firewall device. Example: https://192.168.90.10:4444 (protocol://firewallManagementIp:port) |
User Name | Firewall web login username (We recommend admin credentials) |
| Password | Firewall web login password (We recommend admin credentials) |
Netflow Open Source
- Click Validate button, to test the validity of the device info.
Device credentials and commands are validated and the results are displayed. Refer screen shots in fetch using CLI section.
- Click Save button to apply the values.
Fetch rules for Check Point devices
- Click the Add button to add the device information to fetch the rules and configurations using CLI, API. The Add Device Credentials screen opens up.
- Select the Firewall device in the Select Device drop down list.
Check Point firewall version 80.10 or later with CEF log format cases, we have only option to get IP address value from syslog, in these cases using IP address we can't findout the gateway specific rules, so must provide Gateway Name value to get gateway specific rules. - In the Fetch Through drop down list, there will be options to fetch rules and configurations: CLI, API, File
Select the option as API.
Fetch Through API
- In the API selection, enter the Device Info.
Primary Info - deal with parameters that are necessary to establish communication with the device.
Primary Info
Device Info | Description |
|---|---|
Management Server URL | URL of the API management server of the firewall device. Example: https://192.168.90.10:4444 (protocol://firewallManagementIp:port) |
Login Name | Firewall web login username (We recommend admin credentials) |
| Password | Firewall web login password (We recommend admin credentials) |
| Gateway Name | Enter the Gateway Name. Check Point firewall version 80.10 or later with CEF log format cases, we have only option to get IP address value from syslog, in these cases using IP address we can't findout the gateway specific rules, so must provide Gateway Name value to get gateway specific rules. |
| Domain Name | Select the Domain Name check box. Enter the domain name. |
- Click Validate button, to test the validity of the device info.
Device credentials and commands are validated and the results are displayed. Refer screen shots in fetch using CLI section.
- Click Save button to apply the values.
How to enable SSH option for Stormshield firewall
Procedure to enable SSH option for Stormshield devices:
- Go to SYSTEM > Configuration > FIREALL ADMINISTRATION (tab) page.
- Enable below options in UI:
- Enable SSH access
- Enable password access
- Select ssh option in Listening port : select box
- Click Apply button to save the changes.
Procedure to enable web API in firewalls
How to enable Check Point web API from Management Server
Supported version: Web API option available for Check Point R-80.10 or higher versions.
- Open Check Point Smart Console.
- Go to Manage & Settings > Blades > Management API and click Advanced Settings button.
- Enable Automatic Start and choose All IP address option from Access API calls from field.
- Click push button and restart the management server.
How to enable REST API in Sophos XG firewall
- Go to Authentication > Users to create a new user for the API call. The user type will need to be Administrator and its profile will require read/write permissions. This API user is optional, its purpose is to lock the user down to certain rights in the XG, you can always use the Admin account. sophosXGUser
- As an example, we configured this apiuser to have read/write permissions to the Web & Content Filter configuration. sophosXGProfile
- Go to Backup & Firmware > API to enable the API Configuration and input the IP addresses you will make the call from in the Allowed IP Address field. sophosXGServerIP
- This IP address needs to be in a zone that has access to the HTTPS Admin Services, if not, it needs a Local Service ACL Exception Rule.
- Go to Administration > Device Access to verify its associated Zone or to create a Local Service ACL Exception Rule.
How to enable REST API in Sophos UTM firewall
- Login to the WebAdmin GUI.
- Go to Management > WebAdmin Settings > RESTful API.
- Activate Enable RESTful API.sophosUtmRestAPI.
- Allow API token users and network in Management > WebAdmin Settings > General > Allowed Administrators / Allowed Networks.
How to enable Rest API for PaloAlto device
- Go to Device > Admin Roles and select or create an admin role.
- Select the XML API tab.
- Enable XML API features from the list, such as Report, Configuration, Operational Requests, Commit and Export.
- Select OK to confirm your change.
- Go to Device > Administrators and select or add an admin user using added admin role.
- Select OK to confirm your change.
- Commit the new changes
SonicWall
How to enable Rest API for Sonicwall device
- Navigate to MANAGE | Network > Appliance | Base Settings.
- Scroll to theSonicOS APIsection.
- Select Enable SonicOS API and HTTP Basic authentication options.
- Click Accept.
Procedure to enable Nipper
In the Compliance Report field, the following message appears: 'Unable to generate compliance report. Reason: Failed to locate Nipper. Click here to enable it'. What should I do?
Supported Platform:
- Ubuntu 9.1.10
- Fedora 12
- OpenSuSE 11.2
- CentOS 5.5
Prerequisite:
The GNU/Linux platform requires Qt 4.5 to be installed. Your package manager system should automatically install this for you.
Steps:
- Download Nipper libraries from https://www.manageengine.com/products/firewall/download-third-party-utilities.html according to your platform
- Install the rpm or deb according to your Operating System
- For 8.x versions, connect to Firewall Analyzer web client and type the following URL: 'http://<host name>:8500/fw/userConfig.do'
- For 12.x versions, connect to Firewall Analyzer web client and and Navigate to Settings > Others > User Configuration Settings.
- In that, there is an option to provide the path in which you have installed 'Nipper'. For ex: '/usr/bin/nipper'
- Click on Save link
After performing the above steps, go to Setting > Device Rule > Add Device Info, the option to generate compliance report for the device will be enabled.
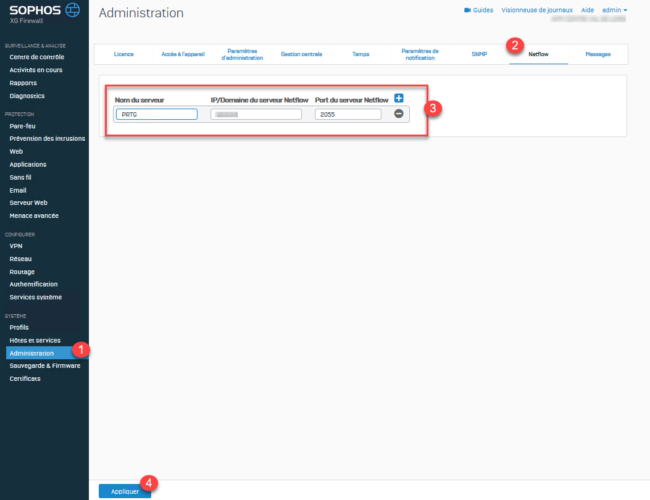
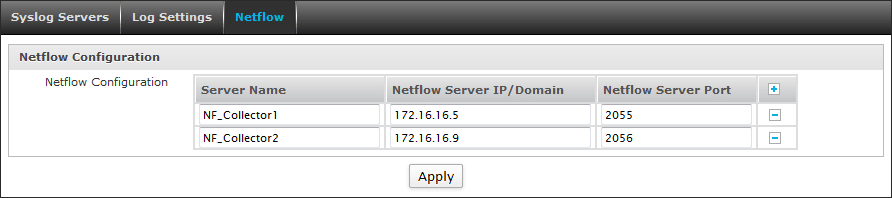
Netflow allows you to add, update, or delete Netflow servers. The device offers Netflow, a network protocol, to monitor network bandwidth usage and traffic flow. Netflow records of source, destination and volume of traffic are exported to the Netflow server. The records help you identify the protocols, policies, interfaces and users consuming high bandwidth. Data analyzing tools like Open Source Data Analyzer and PRTG software can generate reports from the Netflow records.
Netflow configuration
- Enter the Netflow Server name.
- Enter the Netflow server IP/domain. You can enter IPv4 or IPv6 addresses.
- Enter the Netflow server port number (UDP port). Records are sent to the Netflow server over the specified port.
Default: 2055
Sophos Xg Firewall Setup
